Why Infrastructure Decisions Matter
Every outage tells a story. Whether it’s a retail site losing millions on Black Friday, a hospital system going offline during critical procedures, or a ransomware attack halting municipal services, the root cause often traces back to infrastructure decisions.
IT infrastructure is the backbone of digital business operations. Configuring networks, databases, servers, and cloud environments correctly is not just a technical task — it’s a risk management imperative. Misconfigurations or shortcuts can lead to:
- Downtime: Direct revenue loss and customer dissatisfaction.
- Security Breaches: Exfiltration of sensitive data, legal liability, and brand damage.
- Compliance Failures: Fines and restrictions under GDPR, HIPAA, SOC 2, or PCI-DSS.
- Scalability Gaps: Systems that work in year one may collapse under growth pressures.
How to Configure High-Availability Networks, Storage, or Servers
The Goal: Resilience Through Redundancy
High availability (HA) is about designing systems that minimize downtime, even when components fail. The classic “nines of availability” metric (99.9%, 99.99%, etc.) translates directly into annual downtime:
- 99.9% (“three nines”) = ~9 hours per year.
- 99.99% (“four nines”) = ~52 minutes per year.
Network HA Best Practices
- Redundant Paths: Use dual routers, switches, and ISPs with dynamic routing (BGP) to avoid single points of failure.
- Load Balancing: Distribute traffic across multiple servers or services to maintain performance during failures.
- Segmentation: Isolate critical systems from non-critical ones to reduce blast radius.
Storage HA Best Practices
- Replication: Maintain synchronous or asynchronous copies of data across multiple nodes or data centers.
- RAID Configurations: RAID 10 offers strong redundancy, while RAID 5/6 balance cost with fault tolerance.
- Snapshots & Backups: Automate frequent snapshots and store backups in geographically diverse locations.
Server HA Best Practices
- Clustering: Run applications across server clusters for failover capability.
- Virtualization & Containers: Orchestrate workloads with VMware, Hyper-V, or Kubernetes to shift workloads automatically.
- Patch Management: Outdated systems are brittle — regular patching reduces both downtime and risk.
Best Practices for Database Management and Scaling
Why Databases Fail
Databases are often the bottleneck in IT systems. Poor schema design, unindexed queries, or lack of capacity planning can bring entire applications down.
Core Best Practices
- Schema Optimization: Normalize data to reduce redundancy, but denormalize selectively for performance.
- Indexing Strategy: Use primary, composite, and covering indexes to accelerate queries. Avoid over-indexing, which slows writes.
- Capacity Planning: Regularly model query loads and storage growth to anticipate scaling needs.
Scaling Approaches
- Vertical Scaling: Add CPU, RAM, or storage to a single database server. Simple but limited.
- Horizontal Scaling: Shard data across multiple servers or use read replicas to distribute load.
- Caching Layers: Introduce Redis or Memcached to reduce query volume on the primary database.
- Cloud-Native Databases: AWS Aurora, Azure Cosmos DB, and Google Cloud Spanner offer managed scalability.
Monitoring & Maintenance
- Query Profiling: Identify slow queries and optimize them.
- Backup & Recovery: Test restore processes, not just backup jobs.
- Security: Encrypt data at rest and in transit; enforce role-based access controls.
Key Takeaway: Databases require continuous tuning and monitoring — what works at launch will rarely scale to thousands or millions of queries.
Security Hardening of Systems and Endpoints
The Expanding Threat Surface
Endpoints, servers, and cloud workloads are prime targets for attackers. With ransomware and insider threats on the rise, security hardening must be proactive, not reactive.
Server Hardening Steps
- Minimal Installations: Only install necessary services to reduce attack vectors.
- Patch Management: Automate OS and application patching.
- Firewall Rules: Apply least-privilege network access policies.
- Multi-Factor Authentication (MFA): Especially for administrative accounts.
Endpoint Security Best Practices
- Antivirus/EDR: Deploy Endpoint Detection & Response (EDR) solutions for real-time threat monitoring.
- Device Encryption: Enforce full-disk encryption for laptops and mobile devices.
- Access Control: Enforce least privilege and regularly audit permissions.
- Zero-Trust Principles: Never assume trust based on location — authenticate and verify continuously.
Monitoring and Compliance
- SIEM Integration: Aggregate logs into a Security Information and Event Management system for correlation.
- Vulnerability Scanning: Run scans regularly and remediate quickly.
- Compliance Benchmarks: Apply CIS, NIST, or ISO 27001 standards for structured hardening.
Cloud Infrastructure Design (AWS, Azure, GCP)
Why Cloud Architecture Matters
Cloud platforms promise elasticity, agility, and cost optimization — but poor design can lead to runaway expenses, compliance violations, and unexpected downtime. Configuring cloud correctly is about more than spinning up VMs; it requires architecture thinking.
Core Principles of Cloud Design
- Shared Responsibility Model: Understand what the cloud provider secures (infrastructure) versus what you must secure (applications, data, identities).
- High Availability Across Zones: Distribute workloads across availability zones (AZs) and regions to minimize risk of localized outages.
- Auto-Scaling: Configure horizontal scaling rules to match compute resources with demand spikes.
- Infrastructure as Code (IaC): Use Terraform, AWS CloudFormation, or Azure Bicep to make infrastructure reproducible and version-controlled.
AWS Best Practices
- Well-Architected Framework: Follow pillars of security, reliability, performance, cost optimization, and operational excellence.
- Elastic Load Balancing + Auto Scaling Groups: Core tools for HA deployments.
- IAM Policies: Use least-privilege access and rotate keys frequently.
- S3 Storage: Apply lifecycle policies, versioning, and encryption.
Azure Best Practices
- Resource Groups: Organize workloads by project or department.
- Azure Active Directory (AAD): Centralize identity and enable conditional access policies.
- Hybrid Cloud Options: Leverage Azure Stack for edge or on-prem integration.
- Security Center: Continuous compliance monitoring with built-in recommendations.
Google Cloud Best Practices
- Anthos & Kubernetes: Cloud-native orchestration with portability.
- BigQuery: Serverless, scalable data warehouse with pay-per-query efficiency.
- Identity-Aware Proxy (IAP): Enforce zero-trust access models.
- Cloud Spanner: Globally distributed database with strong consistency.
Cost Control Strategies
- Rightsizing: Continuously adjust instance sizes.
- Reserved Instances/Savings Plans: Commit to usage for significant discounts.
- Tagging & Chargeback: Track costs by team, workload, or project.
Case Example: A SaaS company cut its AWS bill by 40% by implementing auto-scaling groups, shifting test environments to spot instances, and enforcing tagging for cost allocation.
Key Takeaway: Cloud infrastructure design should balance resilience, security, and cost efficiency. Skipping upfront design leads to costly retrofits.
DevOps Pipelines and CI/CD Best Practices
Why DevOps Matters
The gap between development and operations has historically been the source of deployment failures. DevOps pipelines bridge that gap, allowing teams to deploy faster, with fewer errors, and with built-in rollback strategies.
Pipeline Stages
- Source Control: Git repositories (GitHub, GitLab, Bitbucket).
- Build Automation: Jenkins, GitHub Actions, Azure DevOps.
- Testing: Unit, integration, and security tests.
- Deployment: Automated rollouts to staging/production.
- Monitoring: Continuous feedback loop into development.
Best Practices
- Infrastructure as Code (IaC): Automate provisioning alongside application deployment.
- Containerization: Use Docker for environment consistency.
- Orchestration: Kubernetes or ECS for scaling and resilience.
- Secrets Management: HashiCorp Vault or cloud-native tools for API keys and credentials.
- Blue/Green Deployments: Deploy new versions in parallel to avoid downtime.
- Rollback Plans: Always have a clear path to revert if a deployment fails.
Security in DevOps (DevSecOps)
- Integrate security scans into CI/CD (e.g., Snyk, SonarQube).
- Automate dependency updates to avoid vulnerabilities.
- Apply principle of least privilege to pipeline service accounts.
Case Example: A financial services company reduced release cycle times from 2 weeks to 2 days by adopting GitLab CI/CD, containerization, and IaC, while improving compliance with automated security scans.
Key Takeaway: DevOps pipelines aren’t just about speed — they’re about predictability, resilience, and security.
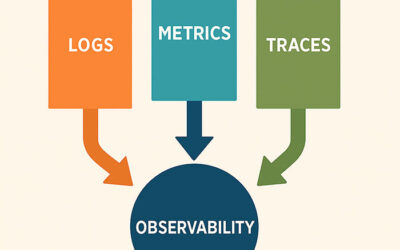
Monitoring, Logging, and Alerting Configurations
Why Monitoring Matters
“If you can’t measure it, you can’t manage it.” Monitoring and logging provide visibility into availability, performance, and security. Without it, IT teams fly blind.
Monitoring Layers
- Infrastructure: CPU, memory, disk, and network utilization.
- Applications: Latency, error rates, throughput.
- User Experience: Synthetic transactions, real-user monitoring.
- Security: Intrusion detection, anomalous login attempts.
Logging Best Practices
- Centralized Logging: Aggregate logs from all systems into ELK (Elasticsearch, Logstash, Kibana), Splunk, or cloud-native services.
- Log Retention: Define policies for compliance (HIPAA, PCI-DSS).
- Correlation: Use logs to connect infrastructure events with user-facing issues.
Alerting Strategy
- Threshold-Based Alerts: Trigger when metrics exceed set values.
- Anomaly Detection: Machine learning to detect unusual patterns.
- Escalation Paths: On-call rotations and escalation policies.
- Avoid Alert Fatigue: Suppress non-critical alerts and focus on actionable issues.
Tool Ecosystem
- Prometheus + Grafana: Open-source monitoring and visualization.
- Datadog, New Relic, AppDynamics: SaaS monitoring for full-stack visibility.
- Cloud-Native Tools: CloudWatch (AWS), Azure Monitor, Google Cloud Operations Suite.
Case Example: An e-commerce firm cut mean-time-to-resolution (MTTR) by 60% after centralizing logs into Splunk and configuring automated PagerDuty alerts for critical KPIs.
Key Takeaway: Monitoring and logging aren’t optional overhead — they’re the early warning system that prevents outages from becoming disasters.
Integration of APIs and SaaS Platforms into IT Ecosystems
The API-Centric Enterprise
Modern IT environments run on APIs and SaaS platforms. CRM systems, HR platforms, marketing automation tools, and ERP systems all expose APIs that must integrate seamlessly into the IT fabric.
Integration Challenges
- Authentication: Managing API keys, OAuth tokens, and SAML assertions securely.
- Data Mapping: Ensuring data models align across platforms.
- Rate Limits: Designing systems that respect API call quotas to avoid service disruptions.
- Versioning: APIs change — systems must handle deprecated endpoints gracefully.
Best Practices
- Use Middleware/ESBs: Tools like MuleSoft, Dell Boomi, or Azure Logic Apps simplify integration.
- Adopt API Gateways: Centralize security, rate limiting, and monitoring (e.g., Kong, Apigee, AWS API Gateway).
- Standardize Authentication: Implement SSO and federated identity for consistent access.
- Monitor Integrations: Log API failures, latencies, and retries.
SaaS Ecosystem Considerations
- Vendor Lock-In: Mitigate risk by designing for portability.
- Data Residency: Ensure SaaS vendors comply with data sovereignty laws.
- Shadow IT: Identify and integrate unofficial SaaS tools that teams adopt.
Case Example: A healthcare organization unified its SaaS stack (Salesforce, Workday, ServiceNow) with an API gateway and Azure Logic Apps, reducing integration overhead and ensuring HIPAA compliance.
Key Takeaway: API and SaaS integration requires governance as much as connectivity — secure, standardized, and monitored interfaces prevent silos and compliance issues.
FAQ: Common IT Infrastructure Questions
Q: What’s the single most important factor in high availability?
Redundancy. Systems must be designed assuming failure. Redundant paths, clustered servers, and replicated storage ensure resilience.
Q: How do I know when to vertically scale vs. horizontally scale a database?
Vertical scaling is quick but capped by hardware limits. Once performance gains flatten, horizontal scaling with replication or sharding becomes necessary.
Q: What’s the best way to secure endpoints in a hybrid workforce?
Adopt zero-trust principles, enforce MFA, deploy EDR, and apply continuous monitoring. Home offices must be treated as hostile networks.
Q: Which cloud provider is best — AWS, Azure, or GCP?
It depends: AWS leads in breadth of services, Azure in enterprise integration (especially with Microsoft shops), and GCP in analytics/AI. Many organizations adopt multi-cloud strategies.
Q: How do I avoid DevOps pipeline failures?
Implement automated tests, enforce peer reviews, manage secrets securely, and always have rollback/blue-green strategies in place.
Q: How do I prevent alert fatigue in monitoring systems?
Prioritize actionable alerts, use anomaly detection, and rotate on-call schedules fairly. Periodic tuning of thresholds is essential.
Q: Why are API integrations so prone to failure?
Dependencies on external services, version changes, and poorly handled authentication create fragility. Centralized gateways and proactive monitoring reduce risk.
Building IT Infrastructure That Lasts
Resilient IT infrastructure doesn’t happen by accident — it’s the result of intentional design across every layer.
- High-availability configurations keep networks, storage, and servers online through failures.
- Scalable database management ensures applications can grow without bottlenecks.
- Security hardening reduces the attack surface and supports compliance.
- Cloud architecture balances resilience, agility, and cost.
- DevOps pipelines accelerate delivery while embedding reliability.
- Monitoring, logging, and alerting provide visibility and faster incident response.
- API and SaaS integrations enable the modern digital enterprise.
For CIOs, CTOs, and IT managers, the implications are clear: infrastructure isn’t just a cost center — it’s a strategic enabler. Done right, it powers innovation, builds customer trust, and sustains competitive advantage.